In this article we will talk about Lync Fabric logs and now to enable circular logging to keep your drive going out of space madness. If you are reading this article, most likely you ran into similar issues.
To enable circular logging, you will need to use following steps
1. log onto Lync FE server via Remote Desktop Protocol (RDP)
2. Make a right click on Windows PowerShell and select | Run as Administrator | press enter
3. Accept UAC warning by clicking yes
4. On the elevated PowerShell command prompt type following | and press enter
|
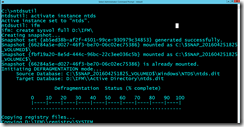
cd ‘C:\ProgramData\Windows Fabric\Fabric\log\Traces’
|
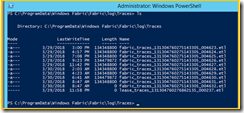
Type following command and press | enter
|
Logman update trace FabricLeaseLayerTraces -f bincirc –cnf
|
6. From PowerShell type | Perfmon | press enter | navigate to following section within the Performance Monitor MMC.
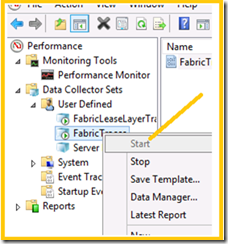
7. Expand Data Collector Sets | Expand User Defined | Select Fabric Traces |
8. Make a right click on |Fabric Logs| and select | Stop|
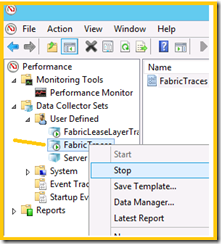
9. Go back to | C:\ProgramData\Windows Fabric\Fabric\log\Traces | location
10. From command line type | Explorer .\ | press enter to open the log directory on GUI
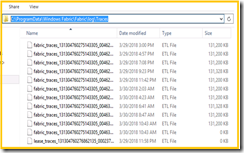
11. Highlight all the existing ELT files and delete them.
12. Go back to Performance monitor snap in
13. This time select | Fabric Traces | on the right pane and make a right click select properties
14. Click File tab on top and locate Circular check box under log mode section
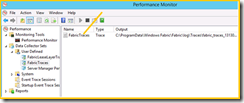
15. Make sure | Circular (requires a non-zero maximum file size) is selected, and is set to ENABLED.
16. If not enable it
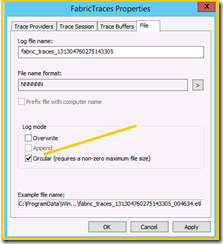 .
.
17. Make a right click on the | Fabric Traces | click on start
Note: You will need to perform same work on all the Lync FE Servers.
Oz Casey, Dedeal
Senior Systems Engineer
http://smtp25.blogspot.com/ (Blog)
https://telnet25.wordpress.com/ (Blog)
https://twitter.com/Message_Talk (Twitter)